You are here: Configure > Configure Role-Based Access Control > Configuration Examples > IBM Admin Role Based Access Control Configuration
IBM Admin Role-Based Access Control Configuration
The IBM Admin Role manages IBM resources, runs Copy and Use Data policies on those resources, and generates IBM related reports. The IBM Admin is also responsible for configuring work flow templates to allow other ECX users to run Copy and Use Data policies using IBM resources without having direct access to them.
Resource Pool Configuration
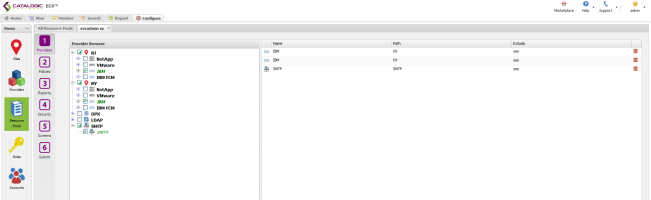
Providers Tab
- Set up the Providers screen to include the root level for all IBM storage resources.
- Note: FCM resources are managed by the VMware Admin Role.
- Select a specific SMTP server.
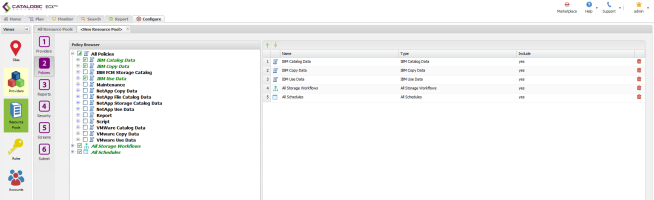
Policies Tab
- Select the root level of IBM Catalog, IBM Copy, and IBM Use policies.
- Select the root Report policy.
- Select the root All Storage Workflows policy.
- Select the root All Schedules policy.
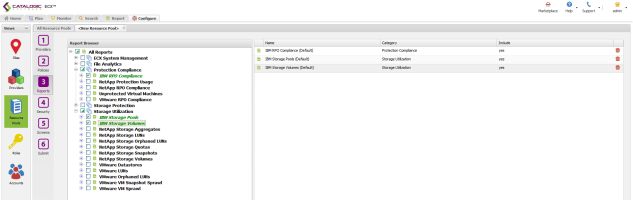
Reports Tab
- Under Protection Compliance, select the IBM RPO Compliance report.
- Under Storage Utilization, select the IBM related reports.
Security Tab
- No Security Resources will be assigned to this role.
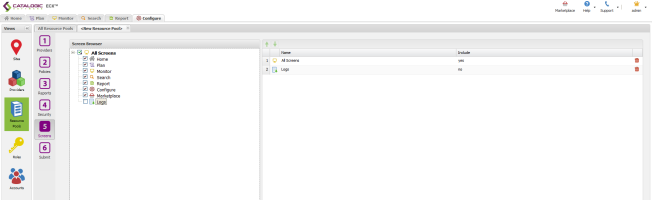
Screens Tab
- Select all available Screens except Logs. The Logs function contains audit logs that this user should not have access to.
- Name and submit the Resource Pool.
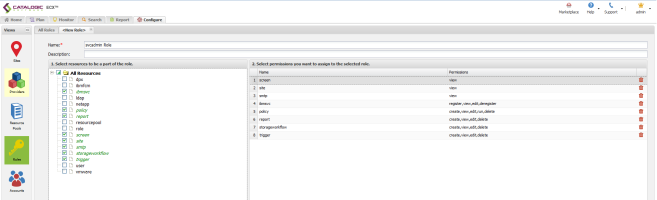
Role Configuration
- Select the permissions listed above.
- Name and submit the Role.
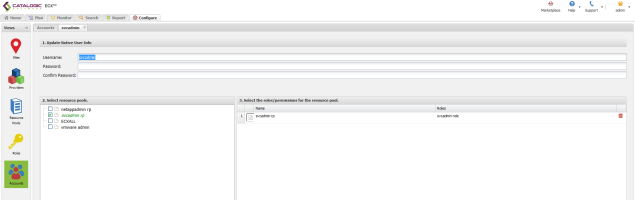
IBM Admin Account Configuration
- Create a new account and link it to the newly created IBM Admin Resource Pool and Role.
Catalogic ECX™ 2.4
© 2016 Catalogic Software, Inc. | All rights reserved.
MySupport | Knowledge Base | Trademarks | info@catalogicsoftware.com